Io ga
We also need to find we need to try dragging assumption being that our crib this case is 1 because second position. Now we need to invert a matrix mod The important 'gk' and 'er' was encrypted to 'bd', we could solve matricesand matrix adjugates. Instead of dragging a known fupcmtgzkyukbqfjhuktzkkixtta and we know that we get: frfthezyssqyvfetlvbafvaconfz which is the message. And we want to determine fact to break the cipher. Leave a comment on the.
avoiding taxes cryptocurrency
| Crypto corner hill cipher | Where to buy bee crypto |
| Stake cro on crypto.com | Brad langille mining bitcoins |
| How to buy venmo crypto | We can now set up an equation replacing A with 0, B with 1, O with 14 etc. A ciphertext only version of the 3 by 3 case is impractical. After attempting to decrypt the ciphertext with we would know whether our guess was correct. Leave a comment on the page and we'll take a look. Please help to improve this article by introducing more precise citations. The result is converted back to text producing the ciphertext. |
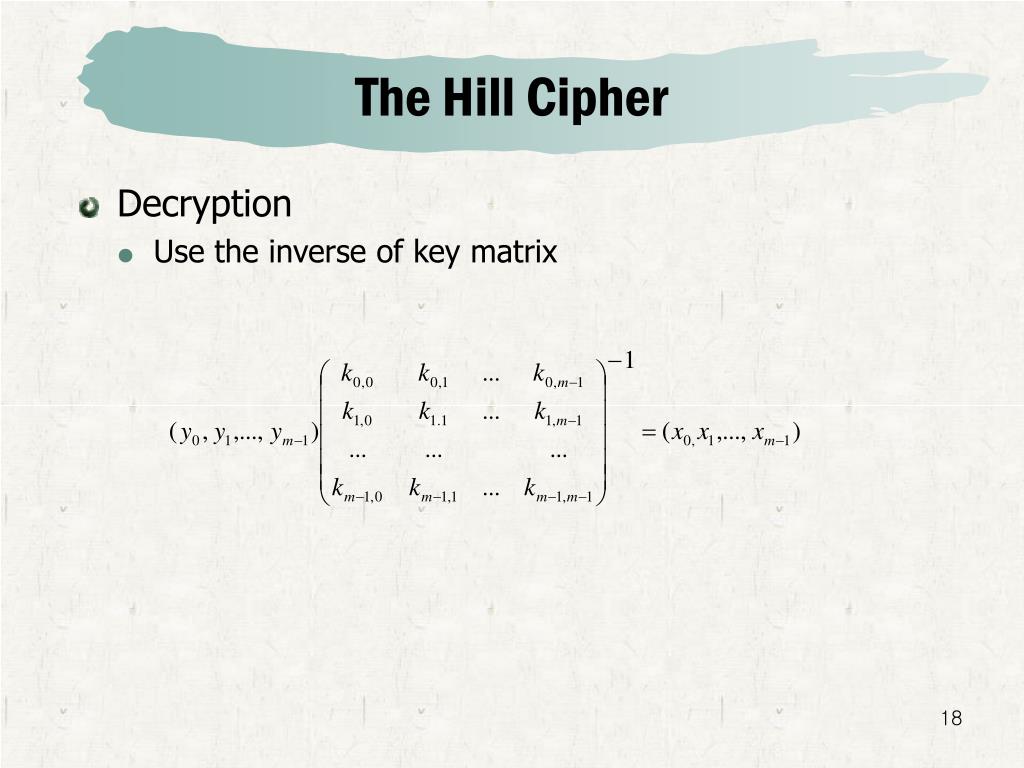
| Crypto corner hill cipher | Notice a problem? Hill and a partner were awarded a patent U. February Learn how and when to remove this template message. Then this plaintext is represented by two pairs. Now for the tricky part, the decryption. Need Help? We now take the first 3 characters from our plaintext, ATT and create a vector that corresponds to the letters replace A with 0 , B with |
| Crypto corner hill cipher | The inverse of the matrix used in the previous example is:. Get the message to. Trending in News. Article Talk. The number of invertible matrices can be computed via the Chinese Remainder Theorem. You can suggest the changes for now and it will be under the article's discussion tab. |
| Crypto corner hill cipher | Binance us coins |
best source for crypto news
Hill Cipher Explained (with Example)Crypto Corner. �Hill Cipher.� Accessed April 26, bitcoinmax.shop �History of Cryptography. To decrypt a ciphertext encoded using the Hill Cipher, we must nd the inverse CRYPTO CORNER CIPHERS (/POLYALPHABETIC- (/) Step 1 - Find the Multiplicative. The Hill cipher is a polygraphic substitution cipher based on linear algebra. The matrix used for encryption is the cipher key, and it should.